Securing Your Business from Cyber Threats: A Complete Guide
July 25, 2023 Category: Business Services
In today’s digital era, businesses of all sizes, from small to medium enterprises in Canada and beyond, heavily rely on the Internet. It’s a vital tool for success, allowing you to connect with new customers, expand your business, and streamline operations. Whether you have a website, social media accounts, or simply use online platforms for banking, payroll, or procurement, the Internet has become an integral part of everyday business activities.
However, with this dependence on the Internet comes a critical need for safety and security. It’s a common misconception that being a small or medium business makes you invisible to cyber criminals. In reality, these businesses often become targets due to the perception of their weaker cyber defenses.
This guide is here to support business owners like you in navigating this complex landscape. Cybersecurity is a collective responsibility. It involves not just owners but also co-owners, managers, and employees—everyone who is part of the business structure and interacts with your digital resources.
Our aim is to equip you with the knowledge and tools to enhance your cybersecurity measures, safeguard your business, and continue to thrive in the digital economy.
Understanding the Threat Landscape
Cybersecurity threats pose one of the most substantial risks to businesses today. From ransomware attacks to data breaches, these threats can have far-reaching implications on a company’s reputation, financial stability, and operational continuity. As cybercriminals have become more sophisticated over time, no business is immune to their attacks. In fact, Statistics Canada reported that 18% of Canadian businesses were impacted by cybersecurity incidents in 2021. These cyber threats are not limited to large corporations; small and medium-sized businesses often find themselves in the crosshairs due to their typically less fortified defenses. The report indicated that 16% of small businesses, 25% of medium-sized businesses, and 37% of large businesses experienced cybersecurity incidents in 2021. This reality emphasizes the importance for all businesses, regardless of size, to bolster their security measures.
According to information from Statistics Canada, the primary types of cybersecurity incidents businesses reported were instances aimed at monetary theft or demanding ransom, along with attempts to steal personal or financial information. When identifying the source of these cybersecurity threats, about 61% of the affected businesses pointed towards external actors. However, it’s worth noting that 38% of businesses could not determine the perpetrator of the cybersecurity incidents.
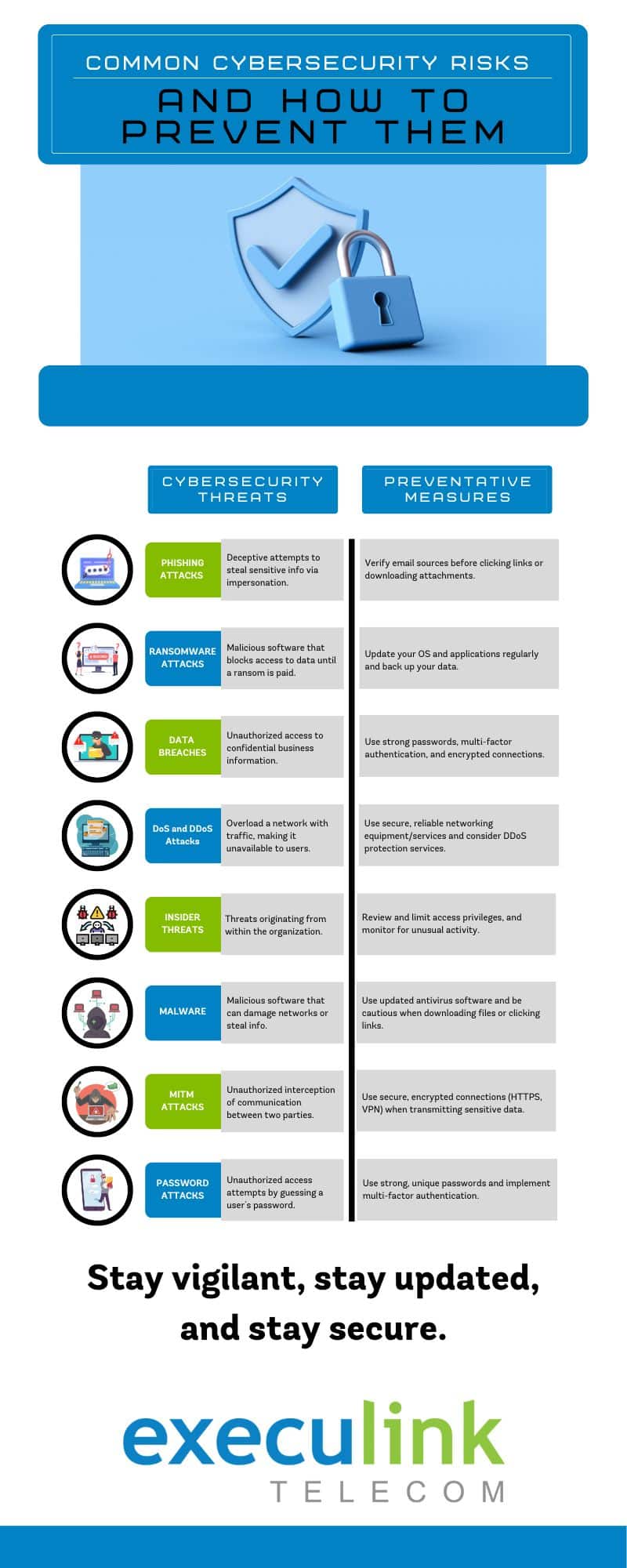
Common Security Risks:
Phishing Attacks: These occur when cybercriminals attempt to trick employees into revealing sensitive information, usually by impersonating a trustworthy entity through email or other communication platforms.
Ransomware Attacks: In these attacks, hackers encrypt business data and hold it hostage, demanding a ransom for its return. The inability to access this data can cause significant disruptions in business operations.
Data Breaches: These involve unauthorized access to confidential business information, leading to significant financial loss, reputation damage, and potential legal consequences. Data breaches can occur due to various reasons, such as weak security protocols or insider threats.
Denial of Service (DoS) or Distributed Denial of Service (DDoS) Attacks: These attacks overwhelm a machine or network resource with traffic, making it unavailable to its intended users. DDoS is a more advanced form where the attack comes from multiple sources.
Insider Threats: These are threats that originate from within the organization. Disgruntled employees or those with malicious intent might misuse their access privileges to compromise the company’s security.
Malware: This term refers to various forms of malicious software, including viruses, worms, Trojans, ransomware, and spyware. Malware can infiltrate a network, damage it, steal information, or create backdoor access.
Man-in-the-Middle (MitM) Attacks: In these attacks, a hacker inserts themselves into a two-party transaction or communication. They can steal data, inject malicious content, or manipulate the communication between the two parties.
Password Attacks: These occur when hackers use software to guess a user’s password, allowing them to gain unauthorized access to a system. This type of attack emphasizes the importance of using strong, unique passwords and implementing multi-factor authentication.
Implementing Robust Security Measures
The first step towards enhancing business security is recognizing that it is an ongoing, proactive process. It begins with implementing a strong security infrastructure, including firewalls, antivirus software, encryption, multi-factor authentication (MFA). Enabling MFA, which acts as an additional layer of security by requiring more than one method of authentication, can greatly reduce the risk of account compromises. Regular software updates are equally important, as they help mitigate the risk of malware that can exploit software vulnerabilities.
A culture of cybersecurity awareness within a business is another key factor in elevating business security. With cybercriminals becoming increasingly opportunistic, it’s crucial that every team member understands the importance of basic security hygiene, which can protect against 98% of cyber-attacks.
Physical Security Measures
While the focus is primarily on cybersecurity, physical security controls are equally important. This includes secure office spaces, controlling access to hardware, protecting against theft or damage, and regularly updating these measures as threats evolve.
Employee Education and Training
Human error is often a significant contributor to security breaches. Training your staff about the importance of security, common cyber threats, and best practices can significantly mitigate these risks. Encourage secure behaviors like complex password creation, avoiding suspicious emails, and not sharing sensitive information.
Regular Software Updates
Keeping software and systems up-to-date is critical. Developers constantly update their software to patch vulnerabilities and improve security. Failing to update can leave your systems exposed to known exploits, making them an easy target for cybercriminals. Despite the ever-increasing cybersecurity threats, it is concerning to note that in 2019, 65% of Canadian businesses did not install security updates for their software and operating systems on a monthly or more frequent basis.
Data Backup and Recovery Plan
The reality is that, despite all your best efforts, breaches can still occur. This makes a robust data backup and recovery plan non-negotiable for every business. Regularly backing up data ensures that you can restore your systems with minimal disruption if a data loss event occurs.
There are several backup and recovery options you might consider. For small businesses with just a few computers, a portable or desktop USB hard drive can be a good starting point. If your business operates on a Local Area Network (LAN), data should be stored on your server and backed up from there.
Alternatively, online backups are available. A secure and reliable environment, like Execulink’s Data Centre, is ideal for storing this data. A Data Centre provides robust security and redundancy, ensuring that your business can continue operating with minimal disruption in case of a system failure or cyberattack.
Whichever method you choose, it’s crucial to back up your data regularly, keep copies of your backups in a secure off-site location, and include system and software settings as part of your backups. Emergency boot disks or USB sticks should be kept ready in case of a system crash, and testing your backups periodically is recommended to ensure the data can be restored if needed.
Disaster Recovery Planning
In addition to data backup and recovery, comprehensive disaster recovery planning is paramount. This includes planning for different types of disasters, from cybersecurity incidents to physical events like fires or floods.
When creating your backup plan, take into consideration what you need to back up, how often, and for how long you need to keep the backups. Remember, some data might need to be kept for specific periods due to legal or contractual obligations.
Through effective disaster recovery planning, you can ensure your business continues operating with minimal disruption, regardless of what calamities may strike.
The Role of Reliable Telecom Services in Security
Reliable telecom services underpin many business operations today, especially in our increasingly connected digital world. However, as essential as these services are, they can also represent potential entry points for cyberattacks. This makes choosing secure and reliable telecom services a fundamental part of your business’s cybersecurity strategy. When considering a telecom provider, look for companies that offer solutions built on a foundation of security, ensuring your private conversations and sensitive data remain private.
The Financial Impact of Cybersecurity
The financial implications of inadequate cybersecurity measures are significant. Notably, the average cost of a data breach in Canada reached $5.4 million in 2021. This figure represents more than just the immediate cost of dealing with the breach; it also includes a variety of indirect costs that can linger for years after the incident.
These costs typically include:
Customer Notification: Informing customers about a data breach isn’t just a courtesy, it’s a legal requirement in many jurisdictions. The process can be expensive, particularly for businesses with a large customer base.
Potential Lawsuits: If the breach results in the exposure of customer information, businesses may face lawsuits. Even if you win the case, the legal fees can be substantial.
Business Disruption: A major breach can halt operations, resulting in lost sales and reduced productivity.
Reputation Repair: After a breach, businesses often need to invest heavily in marketing and public relations to rebuild their reputation and regain customer trust.
To illustrate the magnitude of the issue, businesses affected by a cybersecurity incident spent a total of slightly more than $600 million on recovery in 2021. This represents an increase of about $200 million dollars from 2019, according to a report by Statistics Canada. Moreover, Canadian businesses spend an average of $9.7 billion annually on cybersecurity measures, underscoring the high financial stakes involved.
Enhancing your business security in an age where threats continually evolve is a continuous process. It involves making sure your security protocols are up-to-date, implementing robust measures, and choosing partners that understand and can respond to the changing security landscape. By choosing reliable and secure services, you are taking significant steps towards safeguarding your business’s security and financial stability. Remember, stay vigilant, stay updated, and stay secure.
At Execulink, our aim is to empower your business with the reliable and secure telecom infrastructure it needs to thrive in today’s digital world. Contact us today to learn more.